In the digital information age, data privacy has become a critical concern for individuals and organizations. One significant aspect of data privacy is the right of individuals to access their data held by organizations, commonly referred to as a Data Subject Access Request (DSAR). As regulations such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) enforce stringent requirements for Data Subject Access Request (DSAR) responses, organizations must adopt efficient and compliant processes. This article explores tools and technologies for streamlining DSAR processes, emphasizing the roles of DSAR and Managed Document Review.
Understanding Data Subject Access Requests (DSAR)
A Data Subject Access Request (DSAR) is a request made by an individual (data subject) to an organization (data controller) to access personal data that the organization holds about them. Under GDPR and similar regulations, organizations must respond to DSARs within a specified timeframe, usually within 30 days. This response must include:
- Confirmation that the organization processes the individual’s data.
- A copy of the personal data in a readable format.
- Information on how the data is processed, including the purposes of processing, data retention periods, and third-party data sharing.
Failing to comply with Data Subject Access Request (DSAR) obligations can result in significant fines and reputational damage. Therefore, organizations must ensure their DSAR processes are efficient, accurate, and compliant.
Learn more about DSAR in detail: Navigating Data Subject Access Request (DSAR): Compliance and Best Practices
Challenges in Data Subject Access Request (DSAR) Management
Handling DSARs can be challenging due to several factors:
Volume of Requests
Large organizations often face a high volume of Data Subject Access Requests (DSARs) due to:
- Data Breaches: Breaches prompt affected individuals to submit DSARs to understand data exposure.
- High-Profile Incidents: Publicized privacy incidents increase awareness and DSAR submissions.
- Regulatory Changes: New or amended data protection laws lead to more DSARs.
- Awareness Campaigns: Efforts to inform customers about their data rights increase DSAR submissions.
Efficiently managing these requires robust processes and technologies.
Data Volume and Complexity
Organizations store vast amounts of data across:
- Structured Data: Databases like CRM and ERP systems.
- Unstructured Data: Emails, documents, and social media.
- Legacy Systems: Older, less integrated systems.
- Cloud Services: Multiple cloud platforms with different protocols.
Advanced data discovery tools are needed to locate and extract relevant data efficiently.
Time Constraints
Data protection regulations impose strict deadlines for DSAR responses, usually within 30 days. Key challenges include:
- Acknowledgment: Promptly acknowledging receipt of the DSAR.
- Data Retrieval: Quickly locating relevant personal data.
- Review and Redaction: Ensuring data accuracy and redacting third-party information.
- Response Compilation: Providing the data in an understandable format.
Meeting these deadlines is crucial to avoid penalties.
Compliance and Accuracy
Ensuring compliance and accuracy involves:
- Data Accuracy: Providing accurate, up-to-date personal data.
- Completeness: Including all relevant data.
- Legal Compliance: Adhering to all relevant laws and regulations.
- Privacy Protection: Protecting third-party privacy through redaction.
High compliance standards are necessary to avoid penalties and maintain trust, using robust policies and advanced technologies.
Read Challenges in Fulfilling Data Subject Access Request (DSAR): Balancing Transparency and Data Privacy to understand the challenges in depth.
Tools and Technologies for Efficient DSAR Response
To streamline DSAR processes and address these challenges, organizations can leverage various tools and technologies. These solutions enhance efficiency, accuracy, and compliance in DSAR responses.
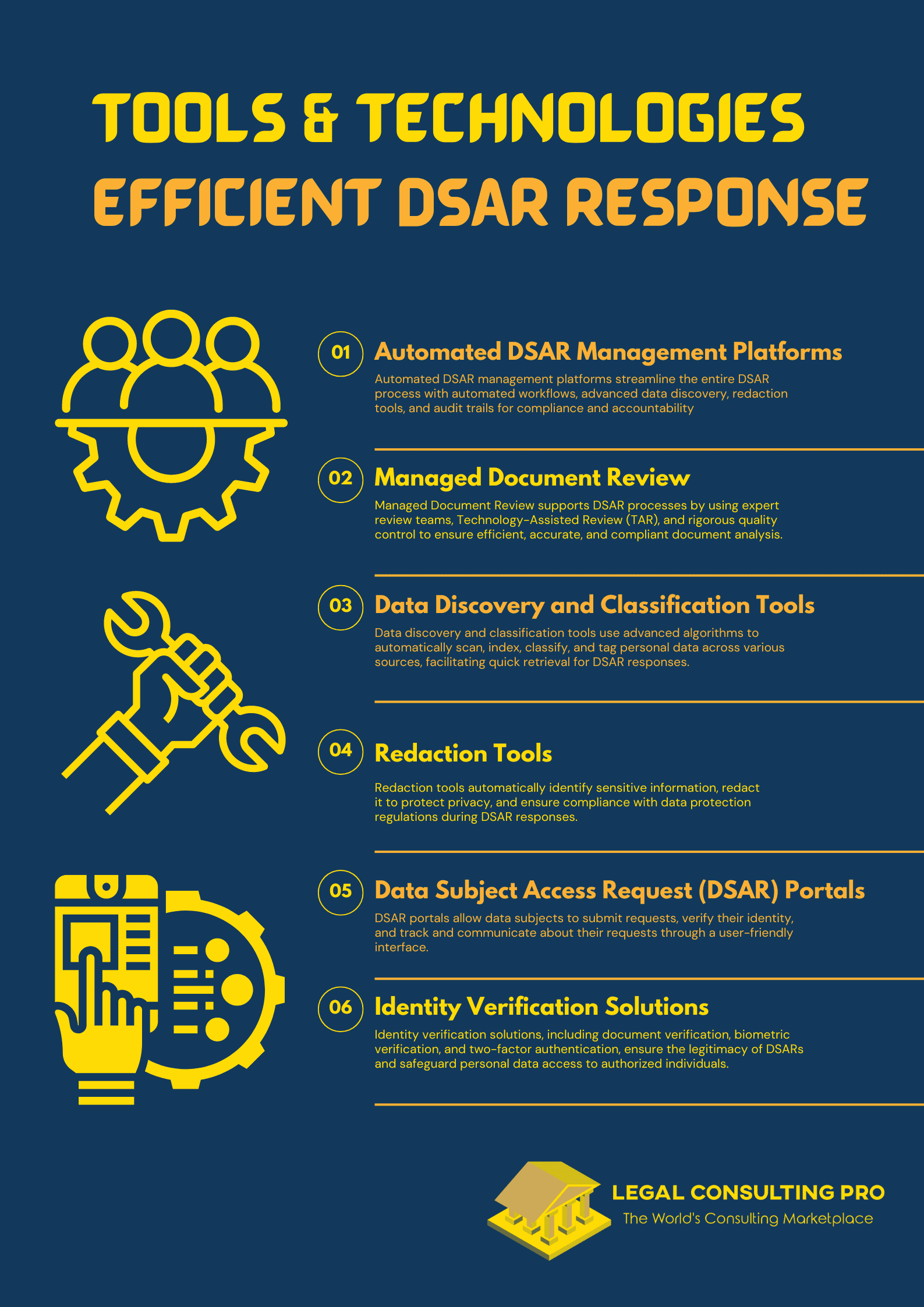
Automated DSAR Management Platforms
Automated DSAR management platforms provide end-to-end solutions for handling Data Subject Access Requests (DSAR). These platforms typically include features such as:
- Automated Workflows: Streamline the DSAR response process by automating steps such as request intake, data retrieval, and response generation.
- Data Discovery: Utilize advanced search capabilities to locate personal data across different systems and databases.
- Redaction Tools: Automatically redact sensitive information from documents to protect third-party privacy.
- Audit Trails: Maintain detailed records of all actions taken during the DSAR process for compliance and accountability.
Examples of such platforms include OneTrust, TrustArc, and Securiti.ai.
Managed Document Review
Managed Document Review plays a crucial role in DSAR processes by providing expertise and resources for thorough and efficient document analysis. Managed Document Review involves:
- Expert Review Teams: Skilled professionals who review and analyze documents to identify relevant personal data and ensure compliance.
- Technology-Assisted Review (TAR): Leverages machine learning and artificial intelligence to expedite the review process by identifying relevant documents and categorizing them based on predefined criteria.
- Quality Control: Ensures the accuracy and completeness of the data provided in response to DSARs through rigorous quality checks.
Managed Document Review services help organizations manage large volumes of data and ensure that responses to Data Subject Access Request (DSAR) are both comprehensive and compliant.
Data Discovery and Classification Tools
Data discovery and classification tools are essential for identifying and categorizing personal data within an organization’s systems. These tools use advanced algorithms to:
- Scan and Index: Automatically scan and index data across various sources, including emails, databases, and cloud storage.
- Classify Data: Categorize data based on predefined criteria such as data type, sensitivity, and regulatory requirements.
- Tag Personal Data: Identify and tag personal data to facilitate quick retrieval during DSAR responses.
Examples of data discovery and classification tools include Varonis, Spirion, and BigID.
Redaction Tools
Redaction tools are critical for protecting sensitive information during DSAR responses. These tools help organizations:
- Identify Sensitive Information: Automatically identify sensitive information such as Social Security numbers, financial data, and third-party personal data.
- Redact Data: Apply redactions to documents to obscure sensitive information before sharing with the data subject.
- Ensure Compliance: Ensure that redactions are performed in compliance with data protection regulations.
Popular redaction tools include Adobe Acrobat Pro, Redactable, and Blackout by Litera.
Data Subject Access Request (DSAR) Portals
DSAR portals provide a user-friendly interface for data subjects to submit their requests and for organizations to manage these requests. Features of DSAR portals include:
- Request Submission: Allow data subjects to submit a Data Subject Access Request (DSAR) through an online form.
- Verification: Implement identity verification mechanisms to ensure that requests are legitimate.
- Tracking and Communication: Enable data subjects to track the status of their requests and communicate with the organization.
DSAR portals streamline the intake and tracking of requests, improving efficiency and transparency in the DSAR process.
Identity Verification Solutions
Identity verification solutions are essential for ensuring that Data Subject Access Requests (DSAR) are legitimate and that personal data is shared only with authorized individuals. These solutions use various methods such as:
- Document Verification: Verify the authenticity of identity documents such as passports and driver’s licenses.
- Biometric Verification: Use biometric data such as facial recognition or fingerprint scanning for identity verification.
- Two-Factor Authentication: Implement two-factor authentication to add an extra layer of security.
Examples of identity verification solutions include Jumio, Onfido, and ID.me.
Best Practices for DSAR Compliance
In addition to leveraging tools and technologies, organizations should adopt best practices to ensure efficient and compliant DSAR responses.
Establish Clear Policies and Procedures
Organizations should establish clear policies and procedures for handling DSARs. This includes:
- Designating Responsibilities: Assigning specific personnel or teams to manage Data Subject Access Request (DSAR).
- Standard Operating Procedures: Defining standard operating procedures for each step of the DSAR process.
- Timelines: Establishing timelines for acknowledging, processing, and responding to DSARs.
- Documentation: Maintaining thorough documentation of all actions taken during the DSAR process for compliance and accountability.
Train Employees
Training employees on DSAR requirements and processes is crucial for ensuring compliance. Training programs should cover:
- Regulatory Requirements: Educating employees on the regulatory requirements for Data Subject Access Requests (DSAR) under GDPR, CCPA, and other relevant laws.
- DSAR Processes: Providing detailed training on the organization’s DSAR policies and procedures.
- Data Protection Principles: Emphasizing the importance of data protection principles such as data minimization, accuracy, and confidentiality.
Regularly Review and Update Policies
Data protection regulations and best practices evolve. Organizations should regularly review and update their DSAR policies and procedures to ensure they remain compliant and effective. This includes:
- Monitoring Regulatory Changes: Keeping abreast of changes in data protection regulations and adjusting policies accordingly.
- Evaluating Processes: Periodically evaluating the effectiveness of DSAR processes and making improvements as needed.
- Incorporating Feedback: Incorporating feedback from data subjects and internal stakeholders to enhance DSAR processes.
Utilize Managed Document Review Services
Managed Document Review services can provide significant benefits for organizations handling Data Subject Access Request (DSAR). These services offer:
- Expertise: Access to skilled professionals with expertise in managed document review and data protection.
- Efficiency: Enhanced efficiency in identifying and extracting relevant personal data from large volumes of documents.
- Compliance: Assurance that DSAR responses comply with regulatory requirements and data protection principles.
Implement Robust Data Governance
Effective data governance is essential for efficient DSAR responses. Organizations should implement robust data governance practices, including:
- Data Inventory: Maintaining an up-to-date inventory of all personal data held by the organization.
- Data Classification: Classifying data based on sensitivity and regulatory requirements.
- Data Minimization: Ensuring that only necessary personal data is collected and retained.
- Data Quality: Ensuring the accuracy and completeness of personal data.
Conclusion
Navigating the complexities of Data Subject Access Requests (DSAR) is a critical aspect of data privacy compliance for organizations. By leveraging advanced tools and technologies, organizations can streamline their DSAR processes, enhance efficiency, and ensure compliance with regulatory requirements. Automated DSAR management platforms, Managed Document Review services, data discovery and classification tools, redaction tools, DSAR portals, and identity verification solutions are key components of an effective DSAR strategy.
In addition to adopting these tools, organizations should establish clear policies and procedures, train employees, regularly review and update policies, and implement robust data governance practices. By combining the right technologies with best practices, organizations can master the art of DSAR compliance and protect the privacy rights of individuals.
Efficiently handling Data Subject Access Requests (DSAR) not only helps organizations comply with data protection regulations but also builds trust with customers and stakeholders. As data privacy continues to be a priority in the digital age, mastering DSAR processes will be essential for organizations to maintain compliance and safeguard personal data.